DJI, the only drone manufacturer in the world to have initiated a Bug Bounty Program, is doubling down on IT security efforts with a special bug bounty incentive. For the rest of this year, security researchers can earn double the maximum payouts possible (up to $10,000) via the DJI Bug Bounty Program.
The DJI Bug Bounty Program
DJI launched its Bug Bounty Program toward the end of 2017 as part of an expanded commitment to work with the research community to proactively discover, disclose, and remediate issues that could affect the security of DJI’s products, applications, and servers. The bounty, thus far, has paid out tens of thousands of dollars to over one hundred researchers.
DJI raised the bounties for server vulnerabilities after noticing that the rate of payouts for server bug vulnerabilities had fallen since 2018. We wanted security researchers to keep finding those bugs, and doubling the size of rewards is a way to focus attention on them. We hope this effort will result in more reports submitted, more server bugs found and remediated, and larger payouts for researchers.
Earning and keeping the trust of our users is a top priority and a close partnership with security researchers allows us to stay ahead of a new generation of hacking tools and at the forefront of consumer data privacy and protection. This is why we are offering higher bounty payouts to qualified DJI contributors who report critical or high-severity server vulnerabilities to us in accordance with the DJI Vulnerabilities Rating Guidelines.
 Vulnerabilities Eligible for Double Rewards under DJI Bug Bounty Program
Vulnerabilities Eligible for Double Rewards under DJI Bug Bounty Program
The bounty range for high-risk issues has been increased to up to $2,000 and reporting a critical server bug could help you earn up to $10,000. If you so consent, your unique contribution will also be recognized on the DJI Security Contributors Wall of Fame and/or in other media.
How to report a bug
The process of reporting a bug is pretty straightforward. You will need to create a testing account here to submit your findings in the given reporting template. While we may contact you to confirm the details of your discoveries, a detailed description of the bugs or vulnerabilities will help us to reproduce the issues and fix them exigently. Please remember we take every report seriously and diligently investigate each vulnerability to address it in a reasonable period of time.
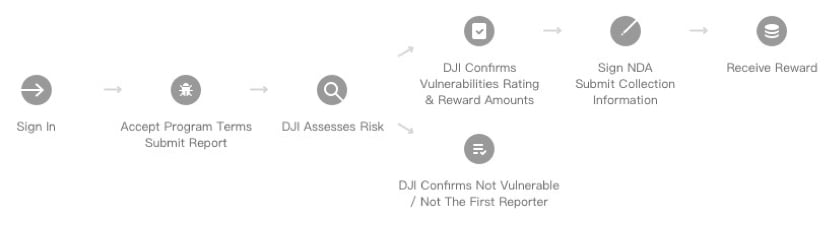 How DJI Bug Bounty Process Works
How DJI Bug Bounty Process Works
An Ongoing Commitment To Cybersecurity and Data Privacy
The DJI Bug Bounty initiative supplements the other powerful measures that we routinely take to bolster data security, customer privacy, and airspace safety, including ensuring that all new products and app software undergo a stringent multistep internal review process.
DJI customers control their data. They alone determine whether to share any of their photos, videos or flight logs with anyone else. Neither DJI nor anyone else can access that data unless customers share it with us, and DJI’s Local Data Mode provides a further level of security by shutting all Internet data transmission from the drone. You can learn more about how to protect your drone data at this link.
DJI’s data security has been independently examined and validated by a wide range of independent reviews. Some are from US federal agencies such as the National Oceanic and Atmospheric Administration, Department of Interior, and Department of Homeland Security. Additional studies by cybersecurity firms Kivu Consulting, Booz Allen Hamilton, and FTI Consulting have found no evidence of any unexpected data transmission from DJI drones. For a greater view into our security protocols and audit reports, visit the DJI Security Response Center.
But remember, you can take advantage of our special bug bounty incentive only until Dec. 31, 2020. Grab full details of the DJI Bug Bounty Program Policy here and act quickly to reap double the rewards!





